A new system, the Swirlds hashgraph consensus algorithm, is proposed for replicated state machines with guaranteed Byzantine fault tolerance. It achieves fairness, in the sense that it is difficult for an attacker to manipulate which of two transactions will be chosen to be first in the consensus order. It has complete asynchrony, no leaders, no round robin, no proof-of-work, eventual consensus with probability one, and high speed in the absence of faults. It is based on a gossip protocol, in which the participants don’t just gossip about transactions. They gossip about gossip. They jointly build a hashgraph reflecting all of the gossip events. This allows Byzantine agreement to be achieved through virtual voting. Alice does not send Bob a vote over the Internet. Instead, Bob calculates what vote Alice would have sent, based on his knowledge of what Alice knows. This yields fair Byzantine agreement on a total order for all transactions, with very little communication overhead beyond the transactions themselves.
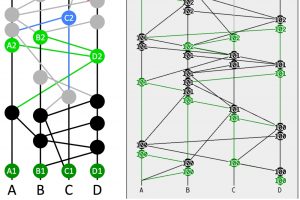
The Swirlds hashgraph consensus algorithm is explained through a series of examples on a hashgraph. Each page shows the hashgraph with annotations explaining a step of the algorithm. This covers the core algorithm, from creating transactions through finding their consensus order and timestamps.

The hashgraph data structure and Swirlds consensus algorithm provide a new platform for distributed consensus. This paper gives an overview of some of its properties, and comparisons with the Bitcoin blockchain. In this paper, the term “blockchain” will generally refer to the system used in Bitcoin, rather than the large number of variants that have been proposed.
The goal of a distributed consensus algorithm is to allow a community of users to come to an agreement on the order in which some of them generated transactions, when no single member is trusted by everyone. In this way, it is a system for generating trust, when individuals do not already trust each other…

How does the Swirlds platform avoid Sybil attacks, where hordes of sock puppet accounts from one attacker can manipulate the system? The short answer is that it uses proof-of-stake internally, but is flexible externally. So it can operate as proof-of-stake or proof-of-work. It can operate as permissioned or not permissioned. It can operate in many other modes, as well. But internally, it is proof-of-stake. Section 1 gives an overview of what that means, and how it works. Section 2 describes one specific scenario: proof-of-stake for an open, non-permissioned system built on a cryptocurrency…

Much has been said about the democratization of technology and how the internet, mobile phones and social media can level the information age playing field. But technology can be an equalizer on a more fundamental level — that of trust. Distributed consensus algorithms enable communities of people, strangers who are both unknown and untrusted, to securely collaborate with each other over the internet without the need for a trusted central server. In the past few years more than a billion dollars have been invested in this type of technology. But why? Why is distributed consensus important? The answer can be found by looking at the differences between a dictatorship and a democracy.


